Network
Secure Access Service Edge (SASE)
Securely connected, everywhere

Key capabilities to keep you protected
In today’s borderless business environment, the challenge isn’t just staying connected; it’s ensuring that every connection is secure, no matter where it occurs. The traditional perimeter-based approach to security no longer cuts it, often leaving businesses entangled in a complex web of vendors, policies, and control platforms.
A Secure Access Service Edge (SASE) is a powerful solution to the challenge of providing reliable, secure connectivity everywhere, whether it’s happening in remote environments, local branches, or expansive campuses.
This is achieved through combining the intelligent capabilities of SD-WAN, the features of state-of-the-art security technologies, and the vigilance of our Security Operations Centre (SOC) to provide a fully managed, cloud-delivered offering.
Secure SD-WAN
SD-WAN combines traditional WAN capabilities with robust security measures to protect your data right at the WAN edge, while optimising network traffic for enhanced performance and end-user experiences. Our centralised management platform makes network configurations and security policy enforcement straightforward across all your sites, from home offices and micro-branches to large campuses.
Zero Trust Network Access
Built on the “never trust, always verify” principle, Zero Trust Network Access (ZTNA) ensures every attempt to connect to your network undergoes strict identity verification. It narrows the attack surface by granting access only to authenticated and authorised users and devices. Unlike traditional VPNs, permissions can be adjusted in real time for each user session.
Centralised Policy Management
With Centralised Policy Management, you maintain a consistent security posture across distributed networks. Regardless of where your data lies or where your team logs in from, this capability allows for swift adjustments to network configurations and security policies in response to emerging threats, compliance requirements, or business shifts, all through a single platform.
Network Automation
Automation empowers your network to be resilient and self-optimising, responding to traffic flows, user behaviour, and potential threats in real time. By automating the scaling of resources, the deployment of security policies, and other tasks, there’s minimal need for human intervention, leading to reduced errors and enhanced network responsiveness.
Cloud Configuration & Management
Cloud configuration and management capabilities allow for swift deployment, monitoring, and optimisation of your network configurations and security policies across your cloud environments. Everything from firewalls to intrusion detection systems is managed through a single control panel, ensuring your data remains consistently protected as networks and threats evolve.
Endpoint Protection
As the first line of defence, our sophisticated endpoint protection technology continuously scrutinises all devices linked to your network against a vast, cloud-stored threat intelligence database. It provides a centralised control system to enforce security policies and protocols, ensuring your data and workflows remain protected, anytime, anywhere.
Cloud Access Security Broker
Acting as a vigilant intermediary, our Cloud Access Security Broker (CASB) makes sure every interaction between your users and cloud applications complies with your security policies. From spotting rogue apps and unauthorised user behaviour to encrypting data, CASB provides comprehensive protection against cloud-based threats.
Secure Web Gateway
Secure Web Gateway (SWG) inspects web traffic in real-time, preventing harmful content from reaching your network and disrupting your operations, whilst enforcing compliance with security policies, standards, and regulations. Applying URL filtering, advanced threat defence, traffic encryption, and other security measures, our SWG ensures staff can safely browse the web.
Data Loss Prevention
Data Loss Prevention (DLP) safeguards your most critical information, whether it’s in transit, in use, or at rest. By examining content and context, our DLP effectively blocks potential data leaks — securing your financial details, personal identification information, and intellectual property from unauthorised access, while ensuring compliance with data privacy standards and regulations.
Firewall-as-a-Service
Firewall as a Service (FWaaS) delivers traditional firewall functionalities and advanced security capabilities directly from the cloud. By filtering incoming and outgoing traffic based on set security policies, FWaaS effectively blocks malicious activities, ensuring secure access for authorised users, while preventing unauthorised entry into your network.

All managed by Orro's Security Operations Centre
With Orro SASE, you confidently expect great outcomes for your organisation. These include:
- Achieving the same high-level of security across all your endpoints
- Ensuring access to resources is always in the right hands
- Delivering superior experiences for end-users everywhere
- Staying compliant with data security standards and regulations
- Cutting the costs and complexity associated with managing multiple vendors and disparate technologies
- Moving away from capital-intensive investments towards a more flexible and scalable OPEX model
What sets Orro SASE apart is the combination and convergence of our One Touch Control (OTC) and SOC platforms. These combined services serve as a central control hub, arming our SOC experts with a comprehensive suite of integrated tools, including sophisticated SIEM systems, automated orchestration, and advanced analytics. Through this arsenal, our team proactively strengthens your network against threats, ensuring swift detection, investigation, containment, and eradication, while simultaneously enhancing network and application performance.
Orro SASE is also unique in how we bring together our experts; our multidisciplinary teams have a tight grasp of the interconnected nature of network and security, tailoring your SASE deployment to your specific needs and goals.
24x7 monitoring & support
Our SOC team keeps a watchful eye on your network traffic, security systems, and device activities, always ready to swing into action at the first sign of an anomaly. Plus, these experts are always on standby to support you with any questions and concerns you have.
Incident Response
Equipped with security information and event management (SIEM) systems, automated orchestration, advanced analytics, and threat intelligence, our SOC promptly detects, investigates, contains, and eradicates threats. Your systems are restored and security enhancements are made to prevent similar incidents from reoccurring.
Maintenance & Updates
A comprehensive programme of maintenance and updates is crucial for keeping your network and security infrastructure in top condition. Our SOC proactively scans for vulnerabilities, applies necessary patches, and updates software to mitigate security risks, optimise network performance, and enhance end-user experiences.
Assessment & Design
The foundation of SASE begins with a thorough assessment of the current state of your network and security infrastructure. Understanding your network traffic patterns, evaluating risk levels, and identifying security gaps are crucial steps for designing a custom-fit SASE architecture for your organisation.
Deployment & Integration
From SD-WAN and secure web gateways to zero trust network access, we ensure your network and security components are deployed across all user locations and cloud platforms. This allows your distributed teams to seamlessly and securely access company resources from anywhere, on any device.
Reporting & Reviews
Data-driven insights on network activity, security incidents, and compliance enables you to evaluate your security posture and make informed decisions. This continuous loop of feedback is key to adapting to new challenges and ensuring your network and security infrastructure meets your objectives.
A powerful alliance bringing you industry-leading security
Comprehensive global threat intelligence
The collective power of Orro and FortiSASE’s threat intelligence ensures comprehensive, real-time defence against new threats.

24x7 vigilance
Orro’s Australian-owned Security Operations Centres provide rapid threat detection and response, along with proactive enhancements to your security posture.
Streamlined management
Bespoke centralised management platform seamlessly integrates with FortiSASE’s solutions to simplify security operations.
Seamless connectivity
Optimise the performance of your cloud and SaaS applications to deliver a smooth user experience.
Agility and scalability
Adapt swiftly to evolving business needs and scale your security solutions as required, with minimal complexity.
Cloud-native security
Fortinet SASE’s cloud-based architecture, with security embedded at its core, safeguards data regardless of where users connect.
Signs you need SASE now
If these challenges resonate with you, it’s time to get serious about SASE.
Security concerns are deepening
Your security measures are struggling to match the pace, volume, and sophistication of today’s cyber threats.
Everyone working from everywhere
Employees connect from everywhere, often from beyond the secure confines of traditional work environments.
The view is obscured
There’s a fog over your ability to monitor threats due to unclear insights into cloud resources and end-user behaviours.
Device access dilemmas
Not all devices on your network are within your control, leaving open doors for potential security breaches.
Silos leading to tool fatigue
The challenge of managing various disjointed security and network technologies has become overwhelming.
Cloud-centric operations
With most of your applications now cloud-based, traditional security solutions no longer fit the bill.
Direct access demand
Your end users expect direct and seamless access to network resources from anywhere and any device.
Compromised user experience
The quality of user experience is declining due to inefficient network performance and restricted access to necessary resources.
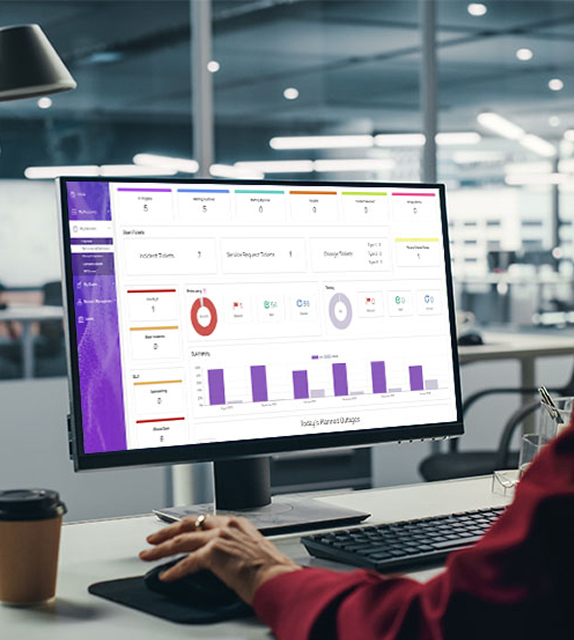
OneTouch Control at the heart of Orro Next-Gen Wireless
OTC provides real-time, end-to-end visibility over your IT estate through one intuitive dashboard. Integrating with industry-leading observability and security tools, OTC gives you actionable insight into your posture for proactive action.
Intelligent incident management
Orro accelerates incident resolution. Automatically generating tickets when an issue has been detected, helps identify the root cause of an issue, and preserves incident data for future trend analysis and enhancements.
AI-enhanced vigilance
The combined AI capabilities of OTC and Marvis are your force multiplier, predicting potential issues before they occur, learning from each incident to enhance future responses, and autonomously managing known issues to minimise human intervention.
Frequently asked questions
Explore our frequently asked questions about our Secure Access Service Edge solutions.
What is SASE?
A Secure Access Service Edge is a framework, not a single deployable product, that combines various networking and security solutions into one cloud-delivered service. Essentially, it involves choosing the perfect mix of tools, platforms, and policies, all tailored to your specific requirements and setup, to guarantee fast, secure, and reliable access to business resources from any location and any device.
What does a successful SASE implementation look like?
Each Secure Access Service Edge implementation is as unique as the business it supports. What’s considered a successful deployment can also vary between use cases. But generally, a successful rollout should enhance the security and performance of your applications and make them much easier to manage. Your SASE partner should be able to showcase client success stories and help you define the right metrics and KPIs for tracking progress.
In addition to the technical aspects of a successful SASE deployment, it’s also important to consider the impact of the rollout on workflows, processes, and communication patterns within a business.
Communication and training should be provided to ensure that everyone understands the benefits of SASE and how it will affect their roles. This will also help foster a culture of collaboration and buy-in from all parties involved.
Regular check-ins and updates should be conducted throughout the deployment process to address any concerns or issues.
Is SASE more expensive and time-consuming to manage than legacy infrastructure?
A Secure Access Service Edge offers a more cost-effective alternative to traditional infrastructure by removing the need for managing hardware and reducing the costs and complexity of dealing with multiple vendors and different technologies. Instead of heavy upfront capital expenditure, SASE moves towards a flexible operating expense model. It also lays down a scalable infrastructure that supports future growth, proving its value as a worthwhile long-term investment.
Will SASE just add another layer of complexity?
Simplicity is one of the key advantages of a Secure Access Service Edge. By integrating various security functions into one cloud-based service, SASE reduces the need for multiple standalone solutions. This centralised approach reduces time spent on system setup, management, and maintenance.
What is the difference between SASE and SD-WAN?
SD-WAN is a networking approach designed to connect users across different locations, usually linking remote branches to a central network, using software-defined networking principles.
SASE, on the other hand, not only incorporates SD-WAN but enhances it by directly integrating cloud-based security services (such as secure web gateways, cloud access security brokers, and zero trust network access) into the network. This means organisations can manage their networks and security from a central platform, significantly simplifying the overall setup.
What are some common SASE use cases?
Workplace transformation
Virtual Private Networks (VPNs) have been the go-to solution for nearly two decades, allowing users to securely access network resources. However, VPNs struggle with handling large numbers of users simultaneously, often becoming overwhelmed, leading to slower application performance and making management more complicated for IT teams.
In contrast, a Secure Access Service Edge, as a cloud-native service, is built for scalability, making it easier to support a large remote workforce. Businesses can adapt rapidly to the needs of remote employees, providing security measures closer to users.
Network modernisation
Traditional security measures weren’t built for the dynamic, cloud-first world we operate in today. A Software-Defined WAN (SD-WAN) intelligently recognises and categorises application traffic right at the network’s edge. It then securely isolates this traffic from the rest. With a Secure Access Service Edge approach, IT teams can upgrade their WANs to provide direct and secure access to apps and services across various cloud platforms, from any location and any device.
High network performance
Legacy networks, designed for a time when data stayed within the safety of corporate data centres, are now outdated. Today, we rely on applications hosted on various cloud services, accessed by a workforce that is both mobile and spread out. This shift beyond the traditional network boundary complicates the task of maintaining top-notch performance and security for vital applications and services.
SASE, a flexible architecture not tied to any one location, enhances network performance by strategically positioning connections closer to where the traffic originates and heads. This setup reduces the number of network hops, decreasing latency, improving overall performance, and lowering the chances for cyber threats to intercept data.
There are plenty more use cases. Get in touch to find out more.
What does the SASE implementation process involve?
Implementing a Secure Access Service Edge requires a planned, phased approach tailored to your organisation’s needs. We start by evaluating your current network and security setup, identifying data locations, security consistency, network visibility, bottlenecks, team skills, and any vulnerabilities.
From this initial analysis, we design a customised SASE strategy, taking into consideration factors like scalability, centralised policy control, support for unmanaged devices, and more.
Deployment is a gradual process, usually starting with addressing your most urgent priorities. We then continuously monitor and adjust your SASE strategy to meet evolving business needs and protect against new threats.
What if I have more specific questions?
Ask away! We’re here to help. Get in touch with us.

The future feels like this.®
A secure network must balance data flow and access with robust security to keep systems and people safe. Our advanced networks deliver greater performance, flexibility and resilience with better bandwidth, more up-time and world-class security.
Trusted Partner
Our customers don’t just trust us to keep them productive and secure today, but to prepare them for what’s next, to grow with them over time and to collaboratively shape their future.
Strategic Advisor
With deep expertise in multiple facets of technology, our customers rely on us to provide them with strategic advice and guidance, helping them make smart moves towards a secure future.
Solution Provider
Our versatile suite of skills enables us to tackle complex challenges for our customers, providing them with complete business solutions that draw from our vast pool of expertise and resources.
Explore our Resources

Beyond Detection: Why OT Recovery Readiness Determines Real Resilience

Orro Awarded 2026 APJ Partner of the Year by Rapid7

Managed Network Service

Threat Hunt: Validating EDR Effectiveness Against Low Noise Remote Access Threats

Vulnerability Backlogs: Why Exposure, Not Volume, Should Drive Security Priorities

AI-Assisted SOC Operations: Why Automation Without Governance Increases Risk

Hybrid & Multi-Cloud Optimisation: Why Resilience Is a Governance Problem, Not a Cloud Problem

Operational Resilience: Why Blast Radius Matters More Than Uptime

Carriage: the hidden foundation of enterprise resilience

AI-Native Foundations: The New Core of Enterprise Resilience

SD-WAN After Go-Live: Why Optimisation Is Where Resilience Is Won or Lost

Just Because You Can Doesn’t Mean You Should
Human-Led, AI-Assisted Security

Taking Back the Keys: Why Self-Custody Will Define Critical Infrastructure Security in 2026

The Rise of the “Chief Integration Officer”

Retail’s Experience Problem: Why AI-Native Networks Are Now a Competitive Advantage

Part 3: Implementing multi-layer visibility over your network and beyond

Part 2: Creating a robust network starts with robust security

Part 1: Building a resilient network for your business

AI-Native Network Readiness Checklist

The Executive Guide to Experience-First Networking

Experience-First Networking: Why User Experience Is the New KPI for Modern Networks

From Firefighting to Forward Momentum: How AI-Native Networking Frees IT Teams
The Shift: Why AI-Native Networking Has Become a Business Imperative

AI Meets OT: Orro’s Perspective on Autonomous Industrial Systems

Operational Resilience Starts at the Edge

Why OT Security Is the New Frontline for National Resilience

When OT Gets Hacked, People Get Hurt

The OT Cyber Resilience Action Plan

Threat Hunt: Scattered Spider

What the ACSC Cyber Threat Report Means for OT Operators

SOCI at a Glance: A Practical Guide for OT Leaders

The IT vs. OT Playbook: A Guide to Productive Collaboration

Navigating the NDB Scheme: A Guide to Data Breach Reporting in Australia

The Australian Business's Cybersecurity Checklist: 10 Steps to Protect Your Assets

The CFO's Playbook: Justifying Cybersecurity Investment

Understanding and Implementing the ACSC's Essential Eight

Phishing in the Australian Context: The Latest Scams to Watch Out For

Beyond the Firewall: Why a Cyber-Resilient Culture is Your Best Defence 🛡️

Threat Hunt: Salt Typhoon

Managing Ransomware Risk: A Practical Guide for Australian Businesses
Cyber Insurance: Is Your Policy Really Protecting You?

Moving to Monitoring to Observability: Unlock the power of your network

Seamless Retail in an Omnichannel World: Building the Infrastructure to Deliver Anywhere, Anytime Experiences

Future-Proof Your K-12: Strategic Technology Planning

K-12 Summer IT Sprint Checklist

Enterprise Voice Services

Microsoft Teams Calling

Summer IT Sprints: A Smarter Way to Build Future-Ready Schools